For labs that are required to follow compliance guidelines, SLIMS provides tehnical controls to securely acquire, process, report, and store data.
Discover more about SLIMS for Pharma






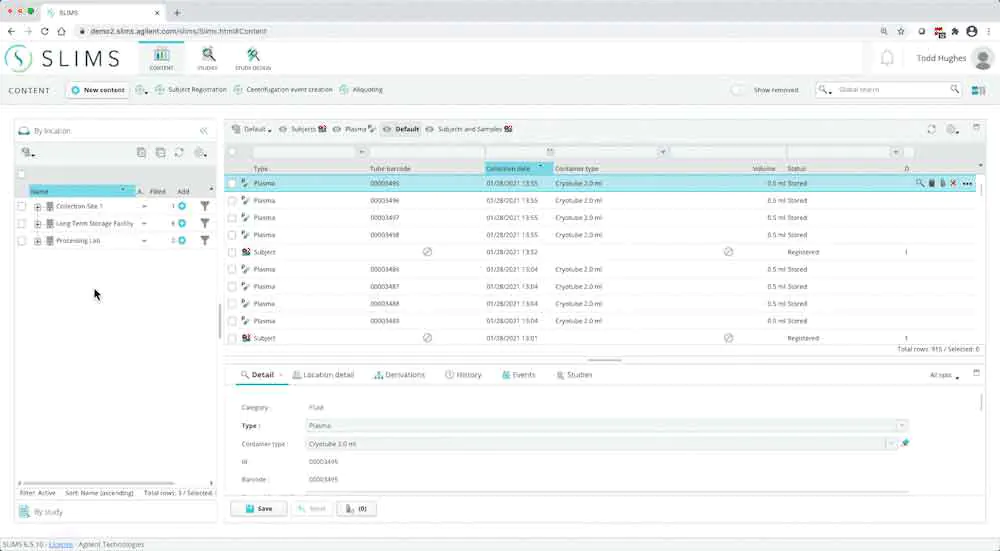
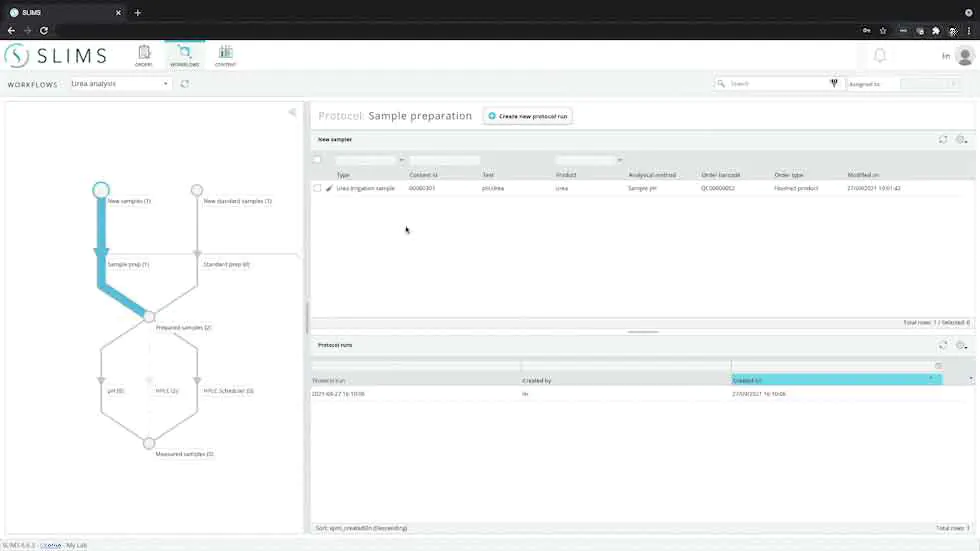

For labs that are required to follow compliance guidelines, SLIMS provides tehnical controls to securely acquire, process, report, and store data.
Discover more about SLIMS for Pharma
Track samples from the initial request through data collection and results reporting, with customized dashboards and end-to-end compliance support.
Discover more about SLIMS for Research Institutes
Design complete studies and automate consent tracking, enrollment, collection events, processing, storage, and more over the entire sample liftime.
Discover more about SLIMS for Biobanks
Provides a single system for integrating sequencers, analysis platforms, and lab software, aiding batch processing and reducing manual intervention.
Discover more about SLIMS for NGS

Covers the entire analytical workflow from request submission to report generation, allowing lab managers to plan, assign, track, evaluate, and more.
Discover more about SLIMS for Analytical Labs
Enhance compliance, traceability, and analysis workflows for cannabis testing labs, from sample intake to potency and safety assessments.
Discover more about SLIMS for Cannabis Testing

“SLIMS became crucial to our activities and is now the keystone of all out operations. SLIMS is used daily by our team members. It not only simplifies our access to data or replaces repetitive tasks, it seamlessly ensures traceability in compliance with our high-quality standards, it integrates analytical equipment to accelerate day-to-day laboratory procedures, and it serves as repository for SOPs and important documentation.”

“SLIMS is a great solution for our biobanking activities. The integrated ELN is an indispensable tool – we use it to track all our sample activities. The SLIMS workflow module is an innovative tool that allows us to register our studies in a dynamic environment. SLIMS is flexible to our needs and a lot of this can be done by the user. Moreover, if we have a complex request or integration issue, engineer support is great.”
LIMS stands for Laboratory Information Management System. When you add "Smart" to this acronym, it becomes SLIMS.
Laboratory information management systems (LIMS) are business applications that manage and track analysis requests and the associated samples, test results, and other information required to issue the final certificate of analysis (COA). LIMS is a general term that covers a wide scope of functionalities and lab markets, but it has been used for years in the industry to describe a system that electronically records samples and results, has workflow functionality, and supports use in regulated environments.
A laboratory execution system (LES) is a combination of LIMS functionality and ELN functionality. It combines the sample centric approach of a LIMS with the workflow driven paradigm of an analytical ELN into a holistic solution for executing laboratory procedures. An LES is the tool of choice for converting paper-based processes into fully automated and integrated digital workflows.
A recent trend in the industry is laboratory digitization. Discover more . Agilent SLIMS combines the flexibility to design your workflow executions, sample tracking, data reporting, instrument integration and more in one holistic application, supported by engineers who help you configure the software and plan for each milestone to minimize disruption to the lab. SLIMS has various install options: it can be run on premise, cloud hosted by Agilent, or cloud hosted by the customer.
It is important to find a LIMS with not only the right features to support complex processes, but one with a team that understands the journey it takes to implement the switch to digital.
The goal of all labs is to be error-free and efficient. Agilent SLIMS brings those benefits to lab operations by reducing manual interface with software. SLIMS provides:
LIMS can be used in various areas, and their coverage differs depending on the domain.
For example, analytical laboratories conducting environmental or food analysis take advantage of holistic workflow management that integrates the best of a LIMS and of an analytical electronic lab notebook into a lab execution system (LES) offering connection to instruments.
Pharmaceutical laboratories gain from regulatory compliance, and a LIMS assists in controlling user inputs, facilitating review by exception, and covering signature needs. A LIMS can even help achieve and maintain ISO 17025 certification, for example.
Biobanks benefit by tracking specimens electronically from sample reception through storage, monitoring, retrieval, sharing, shipment, and delivery. Study management and configurable metadata ensures that all the data related to a sample and its quality are captured and analyzed. Lab automation can be used to make it easier and faster to collect the data.
NGS laboratories need a LIMS to manage their plates through batch processing or to generate libraries. With large amounts of data generated, integration with lab equipment and automation improves user experience, saves time and money, and minimizes errors.
Research labs benefit from interactive note-taking tools like an ELN feature, access rights management and version control, SOPs, and drag-and-drop digital media. Ad hoc protocol templates facilitate data sharing and reuse.
A LIMS provides the laboratory manager with an overall vision of their lab. It shows an overview of the lab that illuminates the operations that might be blocked for different reasons (people, instruments, inventories, or procedures).
Laboratory technicians are guided within the LIMS with step-by-step protocols to help them navigate processes the right way.
Quality assurance specialists need to monitor procedures and quality standards in the lab. A LIMS ensures the lab performs according to their desired regulations.
Principal investigators can manage entire projects with a LIMS and an ELN. With dashboards, they oversee the status of studies and have a perspective on the requests they submit.
Core facility managers can keep their hands in the science, as a LIMS system connects with asset management software so that the results are conveyed to the initial requestor.
The lines between all these different lab tools have increasingly blurred over the last few years, with established LIMS vendors adding ELNs to their portfolio, and ELN vendors adding sample tracking and management capabilities to their products. Learn more.
You should choose a holistic solution that offers the best of a LIMS and ELN in the same tool so you can manage samples from one stage to another, track locations and assignments seamlessly, receive guidance for complex workflows, automate processes to increase efficiency and reduce errors, review by exception, and facilitate collaboration without creating delays. This all-in-one solution is also called a Laboratory Execution System (LES).
"Data should never, ever be written down on paper, a body part, a lab coat, or even a Post-It note. Ensure that data are captured securely by interfaced instruments and that applicable ALCOA+ principles are met." Learn more.
Using a LIMS helps a lab achieve that desired end goal of error reduction and improved efficiency. Use of technical controls in the software assures data quality and data integrity, helping to maintain compliance. Manual procedures such as sample preparation and capture observation tests can be automated, reducing problems and improving the transparency of work. Records and processes are kept more secure by eliminating paper and using electronic signatures.
It's possible to interface analytical instruments so the data they generate can be integrated into automated procedures. For example, instead of writing the preparation of buffer solution in a logbook, the automated process in the LES states what compounds will be required and captures the weights of each electronically. The label containing the buffer name, strength, preparation, and other relevant information are printed on it for the prepared solution and referred to in the LES.
Manual observations are entered into the LES, bypassing paper results entirely, which eliminates the need for master templates and blank forms, and the administrative overhead of managing them. The data is captured electronically, instead of being transcribed, printed, entered in other computer systems, or transferred manually via removable media. Instead, the data is transferred by validated electronic processes, which eliminates the need for transcription error checking. Processes are automated, including the transfer of sample information, requests to the LES to carry out analysis, and results to upload to the LIMS. Either the LES or LIMS can conduct sample management. The CDS and LES are interfaced as well to eliminate manual data entry and transcription error changes.
The cost of compliance is cheaper than that of noncompliance. FDA warning letters show how important it is to automate to the greatest practical degree. Changing to a digital lab is disruptive, but by understanding the principles with help from experts, and with a strategy mindful of those hurdles, the journey to digitization can be achieved a milestone at a time.
Typical LIMS installations require planning, effort, and commitment. Learn more.
Our team of industry experts understands the level of complexity of various labs and how disruptive such a change can be. The implementation of SLIMS is rapid and realistic, transitioning to digital at the lab's pace. We follow a holistic approach focused on time-to-value to prioritize the changes that will improve efficiency from the background and iterate into each next critical milestone to match the lab data model as closely as possible. We install and verify that SLIMS performs exactly as designed, configure the software with the customer, and equip the customer with training to fine tune their transition.
The SLIMS store provides a library of sample types, locations, metadata, automation snippets, sample sheets, and more that customers and our engineers use to make the solution operational quickly. These packages are already configured for specific use in a domain and are ready as is or can be adapted to a specific configuration.
With the SLIMS team and tools, you don't need to purchase days of professional services or highly specialized software engineering expertise to reconfigure or upgrade the software later. You can manage regular maintenance in house.
There are many factors to consider. It depends on the customer’s needs, but some aspects can be guessed when estimating the cost . For example, the number of users, how many functionalities are needed, the method of deployment, and access. SLIMS eases the pain of transition.
Modern software offers flexible installation options. Most LIMS can be installed on a server within your IT infrastructure. Other LIMS are available as SaaS on a scalable, powerful, secure server.
SLIMS lets you choose an implementation between Agilent-hosted or customer-hosted on the cloud, or on premise. SLIMS can be used with just a web browser from a client computer or on a tablet.